Security Breach in a WordPress Plugin «Wordfence Security»
A short side note: This article was made after we shared the breach with the developers of the plugin and received a response from him (the quoted response is in part II of the article).
The article details a simulated hacker attack situation, based on the exploitation of a newly found vulnerability in a popular plugin for WordPress – «Wordfence Security»
Website Configuration
As an example we’ll take a website built on CMS Magento, which has a monthly turnover of $100,000. In addition, the server has a blog built on the CMS WordPress:
www.magento.com/blog (wordpress)
Assume that the blog administrator has blocked the ability to add new plugins and template editing , using the following directives in the “wp-config.php”:
define( ‘DISALLOW_FILE_EDIT’, true );
define( ‘DISALLOW_FILE_MODS’, true );
WordPress Plugin Vulnerability
The hacker gained access to the admin panel of your blog by using brute force or by any of the methods used for hacking.
Analyzing the situation, a hacker in search for possibilities to hack the Magento site management system, will eventually check all the existing plugins on the blog.
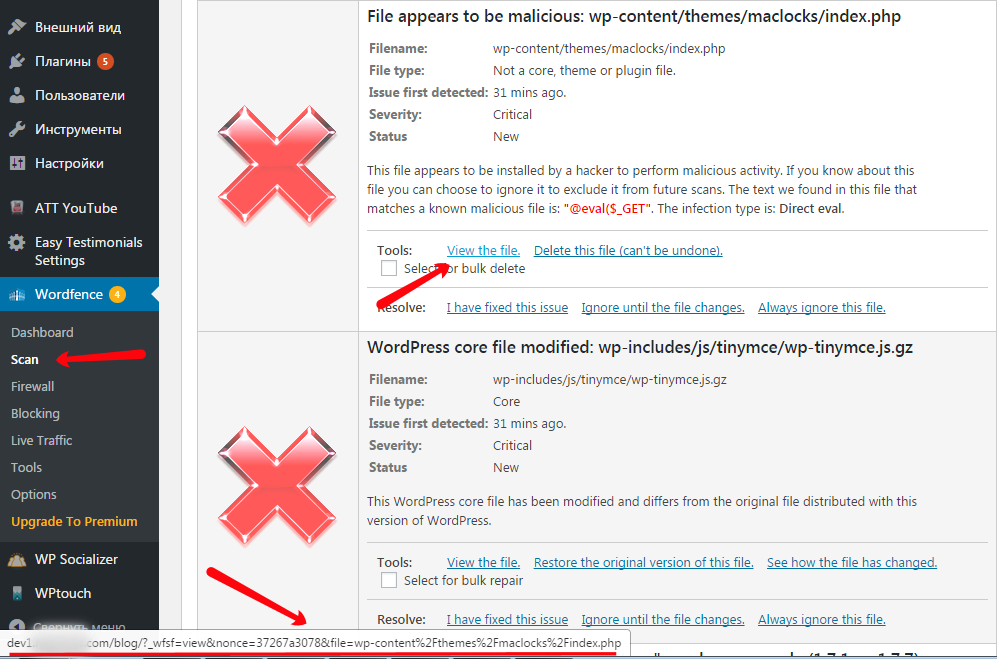
In the website installed plugin “Wordfence”:
This plugin scans for malicious files and is responsible for website security. When the scan is complete, “Wordfence” shows a scan report containing all of the suspicious files.
The screenshot below shows an example of a scan result:
With the help of a built-in tool «View the file», it is possible to view the source file (this is made to make sure if the file malicious or not). Noticing the variable «file» a hacker will in all probability, intuitively inserts the file “index.php”, to see whether it can reach arbitrary files (not related to the results of the scan), as a result he’ll be able to reach the source code.
Gaining Access to the Database
After reaching the Database everything becomes fairly easy – the attacker will inserts the request “wp-config.php”:
https://site-shop/blog/?_wfsf=view&nonce=37267a3078&file=wp-config.php
That, in turn, will reveal all of the sensitive data necessary to access the database:
Next, hacker connects to the site’s database (for example through PhpMyAdmin), and will be able to manipulate all of the data he needs. For example, adding a new administrator to the main Magento website, this will give him additional possibilities for further attacks .