On the basis of the simulated situation we discussed in our previous article, one of our clients found himself in a similar problem.
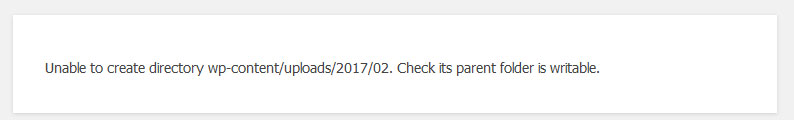
A couple of days ago our client, when attempting to upload a file, received the following error message:
The editing template files and plugin files on the server were also disabled.
Checking which plugins are already installed, we’ve noticed that a “Wordfence Security” plugin was installed.
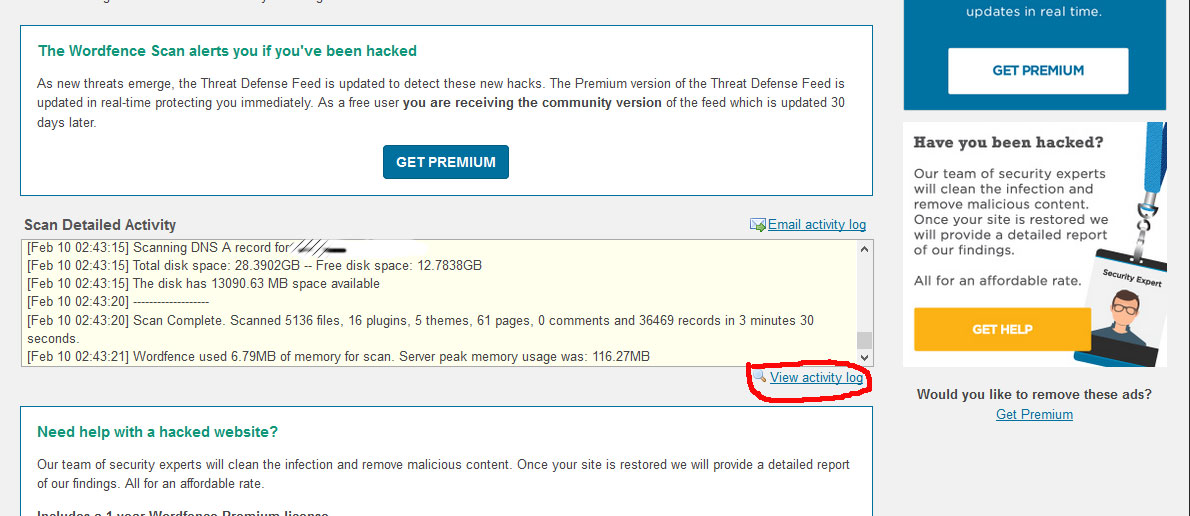
On the “Wordfence Scan” page the report was as following:
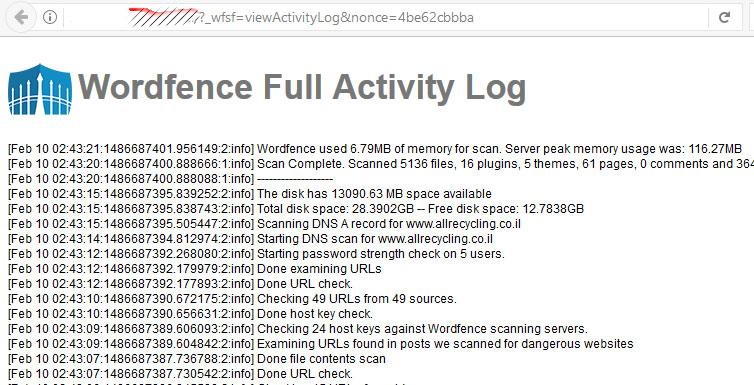
Passing the following link:
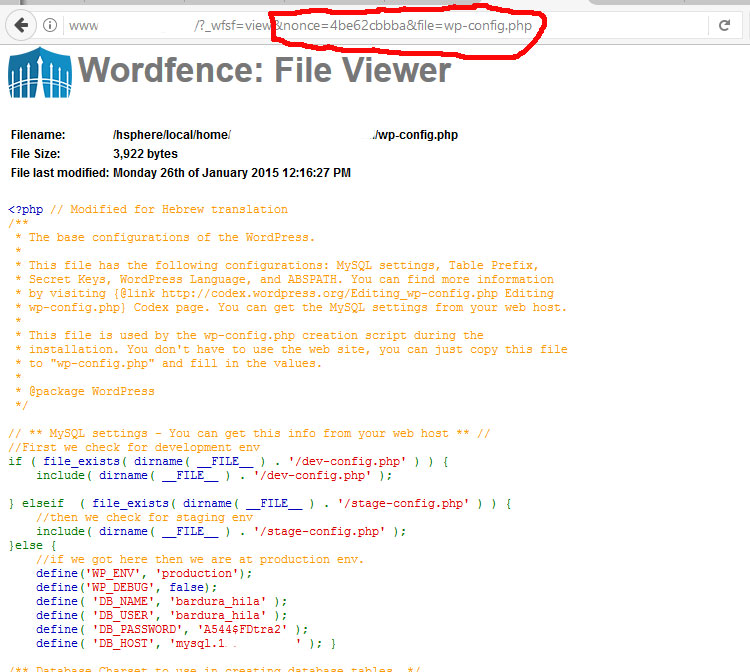
Then everything becomes easy enough – getting token “nonce = 4be62cbbba” ‘, we can go and read files (local file viewer):
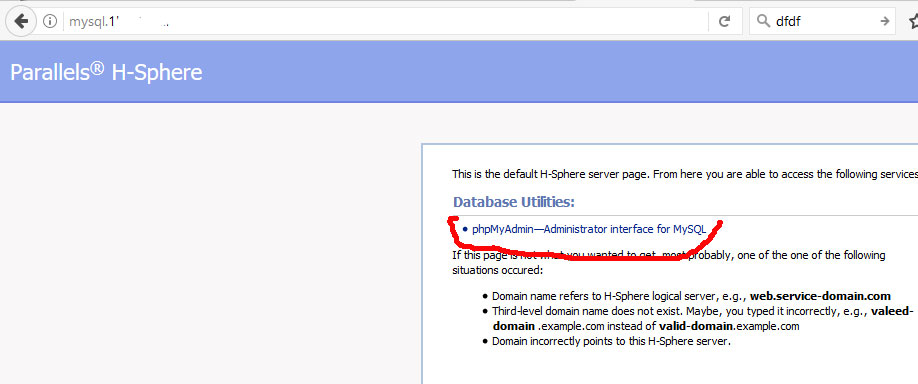
It turned out that PhpMyAdmin located on a different IP address:

MM12345678
grand
Assuming then that perhaps the username and password found in the database – [email protected], suitable for authorization in the admin panel of the website, we decided to check.
The site was on a different server, but it does not matter…
Now we will try to upload the hacker shell through the addition of a specially packed plugin “Hello Dolly” which already contains the shell:
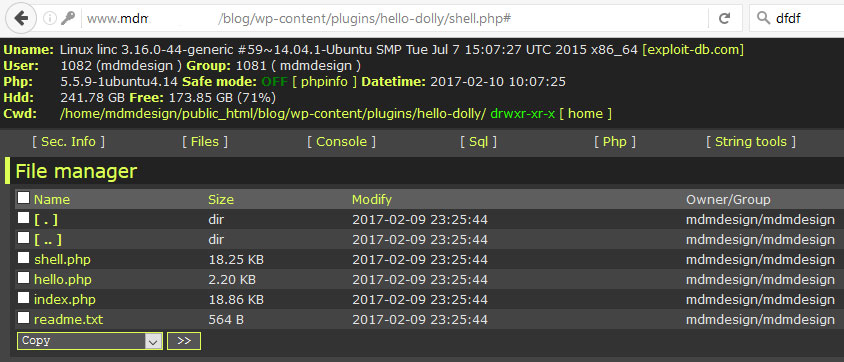
As we can see, the wrong settings of “open_basedir” allowed us to access the root directory, and get the list of sites on the server. In addition, it turned out that the permissions been set to drwxr-xr-x. This allowed us to browse other users on the server.
In conclusion: having gained access to the first website, not only were weable to upload the shell, but also using a security hole in the Wordfence plugin, we were able to use it as a local reader (getting a vector for a new attack).
Thus, we were able to connect to the MySQL database, from where we got the password to a different admin panel (using brute force). Using this technique it is possible to gain access to a dozens of other sites on this server.
P.S.: We reported this vulnerability to Wordfence, but they have decided that this is not a serious problem. At the time of notification plugin version was 6.3, and the problem has not been fixed in the new version of the plugin.
The following is a quoted Wordfence response to our notification message:
“
Hi Amil,
Our file viewer feature, by design, provides more functionality to administrators (or super admins) than a vanilla WordPress installation provides, thus changing the security model of the application. Being able to read the wp-config.php file using an administrator or super admin account is within the scope of this feature.
We’ve discussed internally and have decided to implement our own constant in order to disable this feature should you wish to reduce the access an administrator account has to your installation, much in the same way `DISALLOW_FILE_MODS` allows a developer to disable features at the application level. This will be implemented in one of the next few Wordfence releases.
You are welcome to publish your findings and any part of this conversation.
—
Matt Rusnak
Wordfence Security Team
[email protected]
”